

Fake jQuery Domain Redirects Site Visitors
An in depth look at a piece of malware that redirects victims to a fake malicious website by mimicking a popular domain. It was quite fun researching this fake domain and writing a blog piece on it that is featured on the Sucuri Blog.
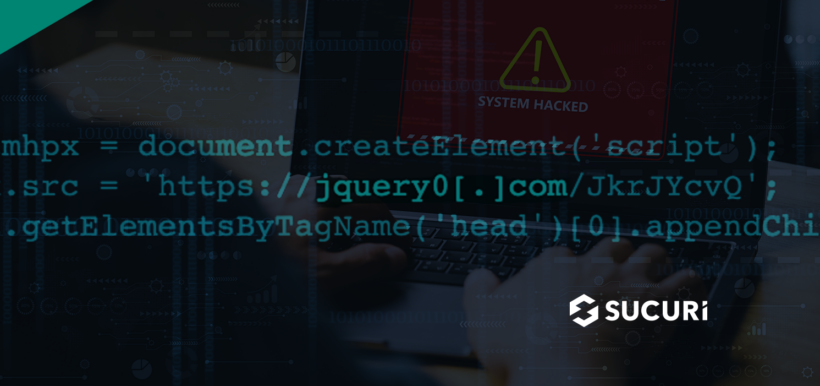
A recent infection has been making its rounds across vulnerable WordPress sites, detected on over 160 websites so far at the time of writing. The infection is injected at the top of legitimate JavaScript files and executes a script from the following malicious domain: https://jquery0[.]com/JkrJYcvQ
At first glance, this domain appears to be legitimate. However, attackers have intentionally selected the domain name with the intention of deceiving webmasters. It’s nearly identical to https://jquery.com — a website belonging to the popular JavaScript library jQuery.
It was quite fun researching this fake domain and writing a blog piece on it that is featured on the Sucuri Blog.
Would you like to read more? Visit the article at the Sucuri Blog.
https://blog.sucuri.net/2022/12/fake-jquery-domain-redirects-site-visitors-scam.html
